
Hello, this time I want to talk about applications that in my opinion is very effective in tracking down and securing the device is lost or stolen, in this case we use the application “Prey” This application was made by Prey Project and Open Source, language courses in making this application ie using Python, we just discussed thoroughly.
Download & Install Prey
1. Through Desktop (PC)
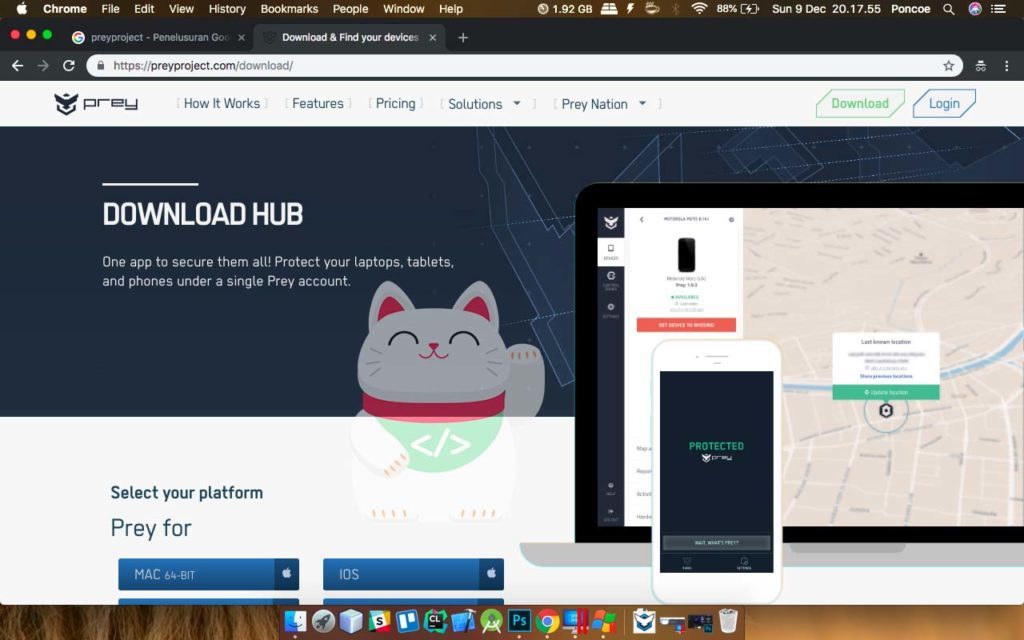
on this site you can download to all operating systems, and it is complimentary and app-in purchase, can Windows, Mac Can, Linux could essentially run in all operating systems. at this time I download for the Mac version. for the site you can download at www.preyproject.com/download
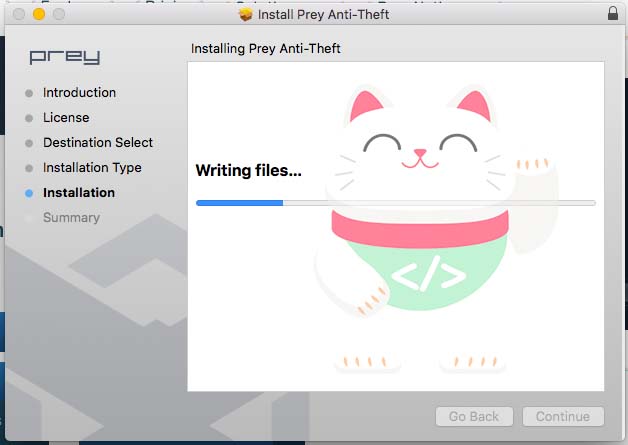
After you download the time you do the installation prey on your desktop device, if completed installation will usually show you a choice of options as a new user or a long-time user, but if on a Mac will automatically open a browser to select the entry as a new user or a long time user.
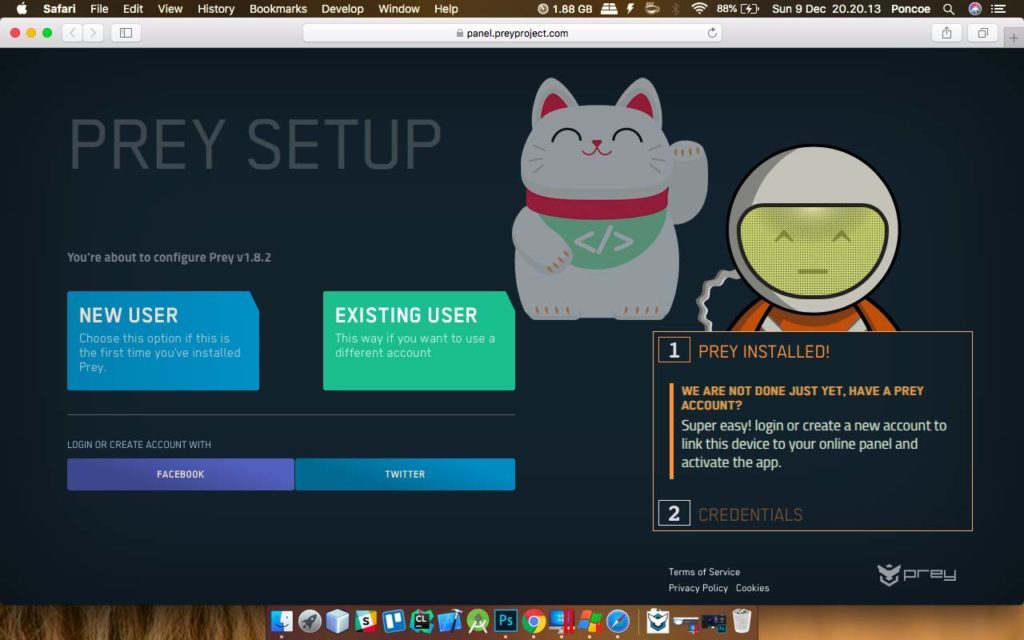
As this result, if on a Mac will open the browser and selecting sign in as a new user or a long-time user, if already logged in will be entered into the control panel and monitor our devices.
2. Through Mobile (Android & iOS)
Welcome to Prey
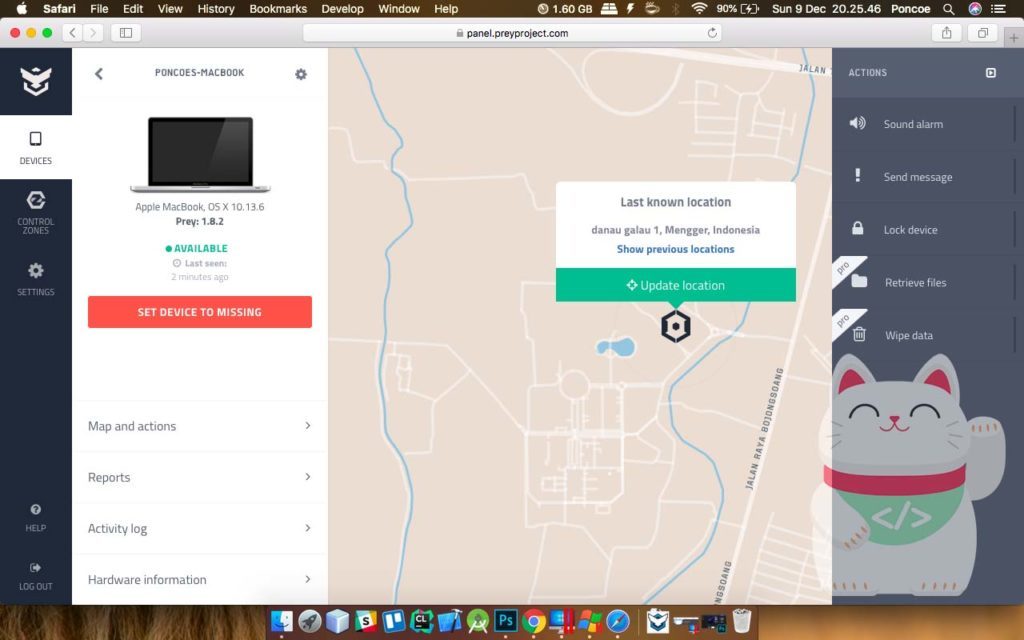
After you download and install Prey on Mobile devices and Desktop, and you have successfully logged in. You will go to the Control Panel to monitor your devices, if diliat of its features like a sizeable kayak Find My Device Google and Find My iPhone from Apple, it’s just more sophisticated really does and in my opinion was quite powerful. Let us discuss its.
1. Sound Alarm
Similar kayak Find My Device Google and Find My iPhone from Apple, just different names aja, if these same features to be bunyiin sound with max volume even in silent mode.
2. Send Message

This allows you to send messages to the device doang heck we were lost, and only nampilin wrote not lock the device, but … in this feature are camouflage. When we press “ok” on the message automatically all our activities are recorded, of Wifi we use, location, secretly photographing us using the front camera and mengscreenshot screen silently and menggirimkan report to us through the account control panel prey , Pretty cool lah.
3. Lock Device
Almost the same in general, which locks the device and only we know password combination to open it.
4. Retrieve Files
for this feature i have not know, and Keith could review feature functions like how it’s going.
5. Wipe Data
This feature is the same as “Erase Data” and all the data on our devices will be permanently deleted through the “wipe data” to save our important data from people who are not responsible.
The final word
after you read this, you’ve got new knowledge in securing a device using a prey, I own use hefty prey of 2015 and secure the one to anticipate the things that i do not want it, maybe that’s all, thank ya





